As they say, "There are two hard things in computer science: cache invalidation, naming things, and off-by-one errors". Out of these 2/3 things, naming is the most difficult. We all know that being lazy when naming things will hurt you down the road when you'll need to make sense of the code that you've written half a year ago. However, one more interesting aspect of good naming paying off I didn't previously think about is memory dump analysis.
Let's imagine, you are facing what looks like a memory leak or some strange behavior of the system and memory dump may help you understand what's happening inside the brain of your system in a particular environment. So you dump your heap, Google Chrome does a great job of grouping your object by constructor name, but all you see is this:
Since your service classes where isolated in your modules/files and you default-exported them, it seemed unnecessary to think of fancy names. The path to the file identifies the service so well anyway! Not until you look at a heap dump like this.
Let's imagine, you are facing what looks like a memory leak or some strange behavior of the system and memory dump may help you understand what's happening inside the brain of your system in a particular environment. So you dump your heap, Google Chrome does a great job of grouping your object by constructor name, but all you see is this:
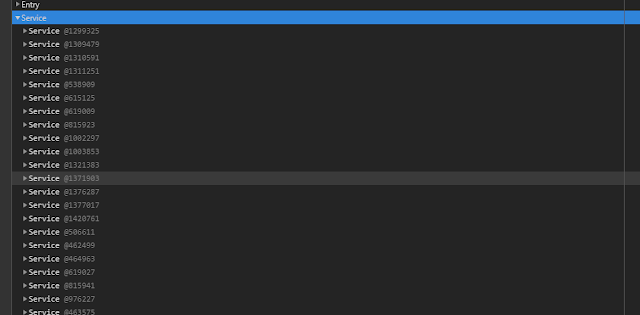 |
| JS heap dump example with badly named constructors |
Comments